October marks Cybersecurity Awareness Month, spotlighting the mounting challenges posed by cybercrimes in 2025. This year has seen an unprecedented escalation in both the number and complexity of attacks, particularly those powered by artificial intelligence, and countries worldwide—led by proactive legislation in places like India—are strengthening their defenses.
Current Cybercrime Landscape
Cyberattacks have surged in 2025, with organizations now facing over 1,900 weekly attacks on average—more than double the figure from just four years ago. Small enterprises report a pronounced lack of cyber resilience, and larger enterprises are continuously adapting to an evolving threat environment. India has encountered a significant increase in cyberattacks affecting government, financial, and healthcare systems, with Advanced Persistent Threat (APT) groups exploiting vulnerabilities in digital infrastructure, sometimes in retaliation to national or political events.
Surge in Cybercrime: 2025 Headlines
India, in particular, has experienced a series of high-profile attacks, targeting government agencies, banks, and healthcare providers.
Massive Cyberattack Campaign Post-Operation Sindoor
Over 1.5 million cyberattacks targeted Indian websites following the Pahalgam terror strike. Seven Advanced Persistent Threat (APT) groups, primarily linked to Pakistan, Bangladesh, Indonesia, and the Middle East, were identified as perpetrators. Although only 150 attacks succeeded, they aimed at critical infrastructure, including government, banking, and healthcare sectors. In the wake of operation Sindoor, Indian agencies responded to millions of intrusion attempts, illustrating the persistent threats to national security and public safety.
“Dance of the Hillary” Malware Spread
A Pakistan-linked malware campaign named "Dance of the Hillary" was uncovered, disseminated via social media platforms. The malware posed significant risks to data security, prompting warnings from Indian intelligence agencies and the Punjab Police.
Star Health Data Breach and Threats
Hacker "xenZen" leaked 7.24 terabytes of sensitive personal and medical data from Star Health, affecting over 31 million customers. The hacker also claimed to have sent death threats and bullets to company executives, citing dissatisfaction with denied medical claims. Malicious Intent, Data theft followed by extortion and personal threats to executives.
BSE Cybersecurity Advisory
The Bombay Stock Exchange issued a cybersecurityadvisory following warnings from CERT-In about ongoing cyber threats linked to Pakistan, targeting India's Banking, Financial Services, and Insurance (BFSI) sector. Malicious Intent, disruption of India's financial systems through cyberattacks.
Telangana Cybercrime Network Bust
The Telangana Cyber Security Bureau conducted a 10-day operation in Gujarat, arresting 20 individuals, including a bank manager, for involvement in a cybercrime network.
- Malicious Intent: Executed large-scale financial fraud through investment, trading, and job scams.
- Unauthorized Access: Operated 27 mule bank accounts to launder illicit funds.
- Digital Target: Victims across India; over 60 cases in Telangana and 515 nationwide.
Hacktivist DDoS Attacks on Indian Organizations
In 2025, Indian organizations across sectors faced a surge in DDoS attacks launched by hacktivist groups. These attacks aimed to disrupt services and draw attention to political grievances. While no data was stolen, the large-scale service outages highlighted vulnerabilities in infrastructure and the growing threat from politically motivated cyber actors.
Nippon Life India Asset Management Cyberattack
Nippon Life India Asset Management reported a cyberattack affecting its operations, emphasizing the vulnerability of financial institutions to cyber threats.
- Malicious Intent: Aimed to disrupt financial services and digital operations.
- Unauthorized Access: Attackers infiltrated NAM India’s IT systems.
Financial Sector Cyber attacks
India's financial sector faced multiple cyberattacks, prompting the Reserve Bank of India to caution lenders and introduce secure domain names to prevent digital frauds.
- Malicious Intent: Aimed to disrupt India's financial infrastructure and erode public trust .
- Unauthorized Access: Hackers infiltrated banking systems, stock exchanges, and financial service platforms .
- Digital Target: Banks, NBFCs, stock exchanges (NSE, BSE), and payment gateways .
- Exploitation of Vulnerabilities: Exploited weak API security, outdated systems, and unpatched software .
- Use of Recognized Attack Vectors: Employed DDoS attacks, phishing campaigns, and malware injections .
PT36 Espionage Threat
APT36, a Pakistan-linked group, leveraged emotionally charged lures post-Pahalgam attack to deliver Crimson RAT malware, targeting Indian defense networks.
- Malicious Intent: Carried out cyber espionage against Indian defense and government sectors.
- Unauthorized Access: Infiltrated systems through phishing emails and malicious attachments.
- Digital Target: Military personnel, defense contractors, and government networks.
Attackers will be able to conduct extensive pre-exploitation reconnaissance by exploiting legitimate credentials. According to IBM’s X-Force Cloud Threat Landscape report, the average price of compromised access credentials has steadily decreased in recent years, going from $11.74 in 2022 to $10.23 in 2024, a 12.8% decrease over a three-year period. These threat actors increasingly use compromised credentials to take advantage of trusted cloud services like OneDrive and Google Drive to distribute malware. IBM’s report offers APT43 and APT37 — North Korean hacking groups — as examples. These individuals have targeted cloud-based services to distribute remote access trojans.
Globally, ransomware remains a dominant threat. Criminal groups are leveraging new sophisticated tactics: attacks not only encrypt data but also threaten public release of sensitive files, intensifying pressure on victims. Ransomware payments have soared, with median figures surpassing $200,000. There’s also been a 58% rise in infostealer malware, much of it powered by AI, designed to infiltrate systems and exfiltrate sensitive data quickly and stealthily.
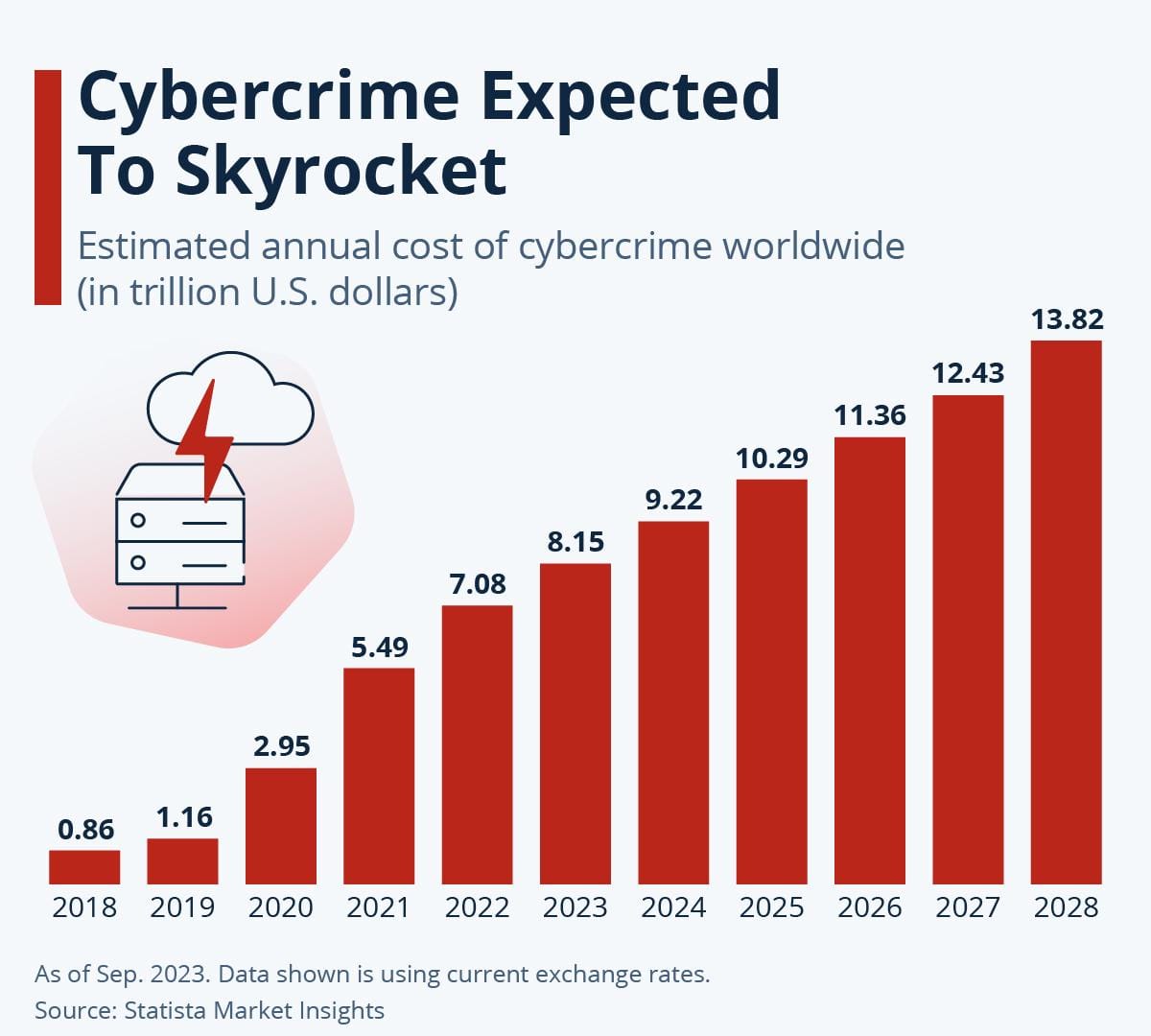
AI and Cyberattack Trends
AI is now a double-edged sword in cybersecurity. While it empowers defenders to detect sophisticated threats faster, attackers leverage AI for creating convincing phishing messages, adaptive malware that evades legacy security tools, and deepfake-led social engineering. Adaptive, AI-powered malware mutates codes in real time, complicating detection and increasing damage, while AI-generated spear phishing campaigns have become highly targeted, tricking even security-conscious users. On the defense side, AI-driven platforms help organizations detect threats faster, analyze vast volumes of data for early warning signals, and respond more effectively to breaches. However, the technology gap between attackers and defenders can create dangerous asymmetries, especially for under-resourced organizations.
Government Mandates and Global Measures
Countries are reacting with urgent and comprehensive strategies:
- Nations now incentivize robust cybersecurity frameworks for critical sectors, mandating regular risk assessments and breach disclosures.
- India, recognizing its vulnerability as the world’s second-largest online market, mandates strict compliance for government, banking, and healthcare sectors. Real-time threat intelligence sharing, regular patch management, and DDoS mitigation are now enforced.
- Globally, policies require organizations to implement network segmentation, AI-driven endpoint protection, and advanced intrusion detection systems. New laws in many regions demand audits, enforce data localization, and establish legal frameworks for rapid incident response.
- The UK and European countries bolster support for allies under attack, providing funding for cybersecurity infrastructure, DDoS defense, and government support for incident response preparedness.
What are the Initiatives Regarding Cyber Security in India
- National Cyber Security Policy: This policy aims to build a secure and resilient cyberspace for citizens, businesses, and the government. It outlines various objectives and strategies to protect cyberspace information and infrastructure, build capabilities to prevent and respond to cyber attacks, and minimise damages through coordinated efforts of institutional structures, people, processes, and technology.
- Cyber Surakshit Bharat Initiative: This initiative was launched to raise awareness about cyber crimes and create safety measures for Chief Information Security Officers (CISOs) and frontline IT staff across all government departments.
- Indian Cyber Crime Coordination Centre (I4C): This centre was established to provide a framework and eco-system for law enforcement agencies to deal with cyber crimes in a comprehensive and coordinated manner. It has seven components, namely:
- National Cyber Crime Threat Analytics Unit
- National Cyber Crime Reporting Portal
- National Cyber Crime Training Centre
- Cyber Crime Ecosystem Management Unit
- National Cyber Crime Research and Innovation Centre
National Cyber Crime Forensic Laboratory Ecosystem - Platform for Joint Cyber Crime Investigation Team.
- Cyber Swachhta Kendra (Botnet Cleaning and Malware Analysis Centre): This centre was launched in 2017 to create a secure cyberspace by detecting botnet infections in India and notifying, enabling cleaning and securing systems of end users to prevent further infections.
- Computer Emergency Response Team – India (CERT-In): It is an organisation of the MeitY which collects, analyses and disseminates information on cyber incidents, and also issues alerts on cybersecurity incidents.
- Critical information infrastructure (CII): It is defined as a computer resource, the destruction of which, shall have debilitating impact on national security, economy, public health or safety.
-
- The government has established the National Critical Information Infrastructure Protection Centre (NCIIPC)to protect the CII of various sectors, such as power, banking, telecom, transport, government, and strategic enterprises.
- Defence Cyber Agency (DCyA): The DCyA is a tri-service command of the Indian Armed Forces that is responsible for handling cyber security threats. It has the capability to conduct cyber operations, such as hacking, surveillance, data recovery, encryption, and countermeasures, against various cyber threat actors.
Essential Defense Strategies
To counter these threats, organizations and governments are urged to:
Prioritize Vulnerability Patching
Patching remains the best defense against cybercriminals. However, many cybersecurity teams neglect it. In 2023, 23% of organizations worldwide experienced cybercrime due to an unpatched vulnerability, making it the leading cause of cyberattacks.
Industrial cybersecurity professionals cannot overlook vulnerability patching. Even if IT/OT convergence complicates their duties and increases their workload, they must prioritize patching known exploits to minimize risk.
Enforce the Principle of Least Privilege
Cybersecurity teams should not implicitly trust any system, device or person — especially if their facility has industrial remote access configured. Since nation-state breaches often leverage legitimate credentials and LOTL techniques, they cannot be too careful.
Utilize Encrypted Multifactor Authentication
Multifactor authentication is an excellent defense against pre-positioning. It prevents network infiltration, thereby mitigating data exfiltration and malware injection. Moreover, it requires little expertise, making it ideal for all employees.
Enabling multifactor authentication comes with one caveat. Team leaders must ensure the communication channel is secure. The FBI has warned Salt Typhoon — a hacking group linked to China — infiltrated at least eight telecommunications providers from 2022 to 2024.
This is one of the largest intelligence breaches in the country’s history. Salt Typhoon may still be actively infecting telecommunications networks. Rich Communication Services (RCS) and Short Message Service (SMS) are not entirely secure. Leveraging an encrypted alternative is crucial.
Secure or Discontinue Remote Desktop Protocol
Industrial firms often rely on remote desktop protocol despite its well-known security weaknesses. Whether they actively use it to simplify troubleshooting or simply forget it was enabled, it poses a serious threat. It must be secured — and should be disabled.
Establish a Cyber Security Board
India must establish a cyber security board with government and private sector participants that has the authority to convene, following a significant cyber incident, to analyse what happened and make concrete recommendations for improving cybersecurity. Adopt a zero-trust architecture, and mandate a standardised playbook for responding to cybersecurity vulnerabilities and incidents. Urgently execute a plan for defending and modernising state networks and updating its incident response policy.
Strengthening Existing legal Framework
India’s primary legislation governing cyber crimes is the Information Technology (IT) Act of 2000, which has been amended several times to address new challenges and threats. However, the IT Act still has some gaps and limitations, such as the lack of clear definitions, procedures, and penalties for various cyber offences, and the low conviction rate of cyber criminals. India needs to enact comprehensive and updated laws that cover all aspects of cyber security, such as cyber terrorism, cyber warfare, cyber espionage, and cyber fraud.
CONCLUSION
Ultimately, no system is 100% secure. Cybersecurity leaders must do what they can to preserve privacy and security where it matters. Perimeter security is a thing of the past — especially if attackers use third parties as a jumping pad. Deploy advanced, AI-powered threat detection and response systems. Regularly update and patch systems to close vulnerabilities quickly. Segment networks and implement VPNs to reduce lateral attack movement. Train employees on best practices, including recognizing phishing and deepfake threats, Support and adhere to strict legal frameworks and industry.
Sources
https://www.weforum.org/stories/2025/09/cybersecurity-awareness-month-cybercrime-ai-threats-2025/
https://eventussecurity.com/cybersecurity/india/cyber-attacks/
https://gca.isa.org/blog/defending-against-state-sponsored-cyberattacks-in-2025
https://www.drishtiias.com/daily-updates/daily-news-editorials/india-s-cybersecurity-challenge-threats-and-strategies

